Advanced Threat Monitoring Solutions
Real-time detection and response powered by AI to protect your critical business assets
See threats before they become breaches
Our platform continuously analyzes your digital environment to detect anomalies and potential threats in real-time.
-
360° Visibility
Comprehensive monitoring across networks, endpoints, and cloud
-
AI-Powered Detection
Machine learning identifies emerging threats before signature updates
-
Automated Response
Instant containment actions reduce attacker dwell time
Comprehensive Threat Protection
Key capabilities that set our solution apart
Network Traffic Analysis
Monitor all inbound and outbound traffic for suspicious patterns and potential data exfiltration attempts with deep packet inspection.
- Detects unusual data transfers
- Identifies command & control servers
- Flags port scanning activities
Endpoint Protection
Continuous monitoring of all endpoints for malicious activities, vulnerabilities, and compliance violations across your organization.
- Process behavior monitoring
- File integrity checking
- Memory protection
Cloud Security
Specialized monitoring for cloud environments and SaaS applications with context-aware threat detection.
- Misconfiguration detection
- Unauthorized access alerts
- Shadow IT discovery
User Behavior Analytics
Identify compromised accounts and insider threats through behavioral analysis and anomaly detection.
- Anomalous login detection
- Privilege escalation monitoring
- Data access pattern analysis
Vulnerability Scanning
Continuous assessment of systems for known vulnerabilities and configuration weaknesses.
- CVE database integration
- Patch management tracking
- Configuration auditing
Threat Intelligence
Integrated feeds from global threat intelligence sources enriched with contextual data.
- Real-time IOC updates
- Emerging threat alerts
- Industry-specific risks
Advanced Threat Detection Flow
AI-powered pipeline that identifies and neutralizes threats in real-time
Data Aggregation
Comprehensive collection of logs, network traffic, and system activities from all endpoints and cloud environments.
AI Analysis
Machine learning models process data streams to detect anomalies with contextual awareness.
Automated Response
Immediate containment actions while alerting your security team with prioritized incidents.
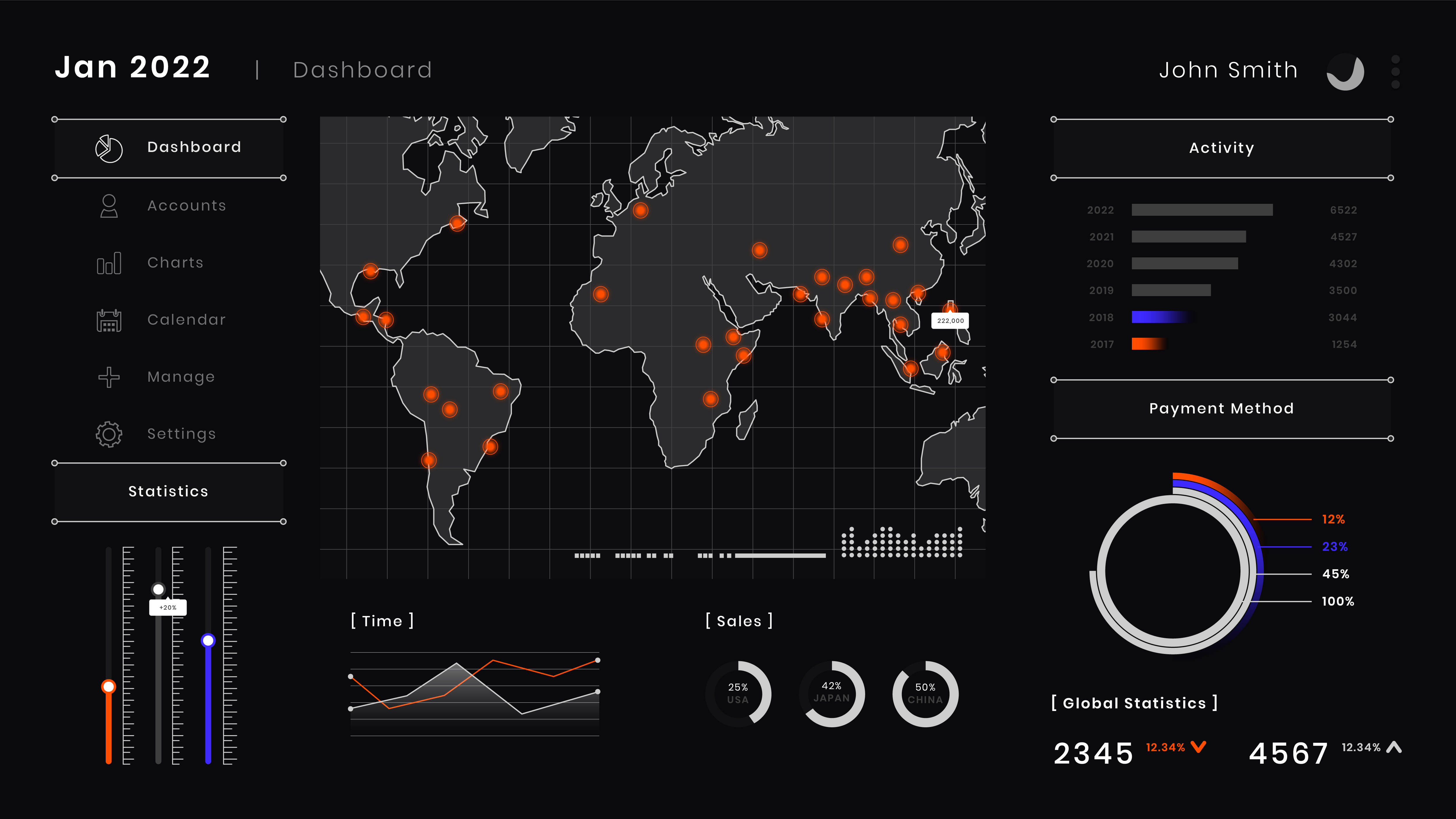
Actionable Threat Intelligence
Our security dashboard provides real-time visibility with contextual insights
Real-time Visualization
Interactive threat maps and activity timelines that update continuously as new data arrives.
Customizable Alerts
Threshold-based notifications that can be tailored to your specific environment and risk tolerance.
Trend Analysis
Historical data visualizations to identify patterns, track improvements, and measure security posture over time.
Comprehensive Threat Coverage
Protection against modern attack vectors
Ransomware
Phishing
Insider Threats
DDoS
Zero-Day
Data Exfiltration
Seamless Ecosystem Integration
Works with your existing security stack
Our solution integrates via API with all major SIEM, SOAR, and endpoint protection platforms to enhance your existing security infrastructure without requiring replacement.
Trusted by Security Leaders
What our customers say about our threat monitoring
"Reduced our mean time to detect threats from 72 hours to just 15 minutes, fundamentally changing our security posture."
Sarah Johnson
CISO, Financial Services
"The AI-powered anomaly detection identified an advanced persistent threat that had evaded our other security tools for months."
Michael Chen
Head of Security, Healthcare
"Automated response capabilities reduced our incident containment time by 90%, saving millions in potential damages."
David Rodriguez
VP IT, Retail
Monitoring Coverage
Detection Accuracy
Average Alert Time
Threat Types Detected
Let's secure your digital future
Our team is ready to discuss your security needs and answer any questions.
Other ways to reach us
Prefer direct communication? We're available through these channels.
Visit Us
Headquarters
Islamabad ,PakistanSOC 2 Certified
ISO 27001
Gartner Leader
